Written by Marijn Overvest | Reviewed by Sjoerd Goedhart | Fact Checked by Ruud Emonds | Our editorial policy
What is Third-Party Risk Management?

As taught in the Risk Management in Procurement Course / ★★★★★ 4.9 rating
What is third-party risk management (TPRM)?
- TPRM identifies, assesses, and controls the security, compliance, and operational risks that arise when your organization relies on external vendors.
- It involves vetting, contracting, monitoring, and auditing suppliers so their vulnerabilities don’t become your data breaches, regulatory fines, or service outages.
- Put simply, TPRM is the framework that keeps your entire vendor ecosystem aligned with your company’s risk appetite and legal obligations throughout onboarding, ongoing operations, and offboarding.
What Is Third-Party Risk Management?
Third‑Party Risk Management is the disciplined process an organization uses to identify, assess, mitigate, and continuously monitor the risks introduced by external vendors, suppliers, contractors, and other partners. It weaves cybersecurity, operational, financial, legal, and reputational controls into due diligence, contracting, onboarding, ongoing surveillance, and off‑boarding activities across the vendor lifecycle. The goal is to keep residual third‑party risk within the firm’s tolerance while enabling compliant, resilient, and cost‑effective collaboration.
Regulators such as GDPR and CCPA also hold you liable for your vendors’ missteps, making fines and legal action a real possibility. On top of that come breach-recovery costs, SLA penalties, lost revenue, and lasting reputational damage, so managing third-party risk is essential.
Third-Party Risk Management Lifecycle
A comprehensive Third-Party Risk Management program follows a structured lifecycle to identify, assess, control, and monitor risks arising from vendor relationships. While exact phase names vary, most organizations break the lifecycle into six key stages:
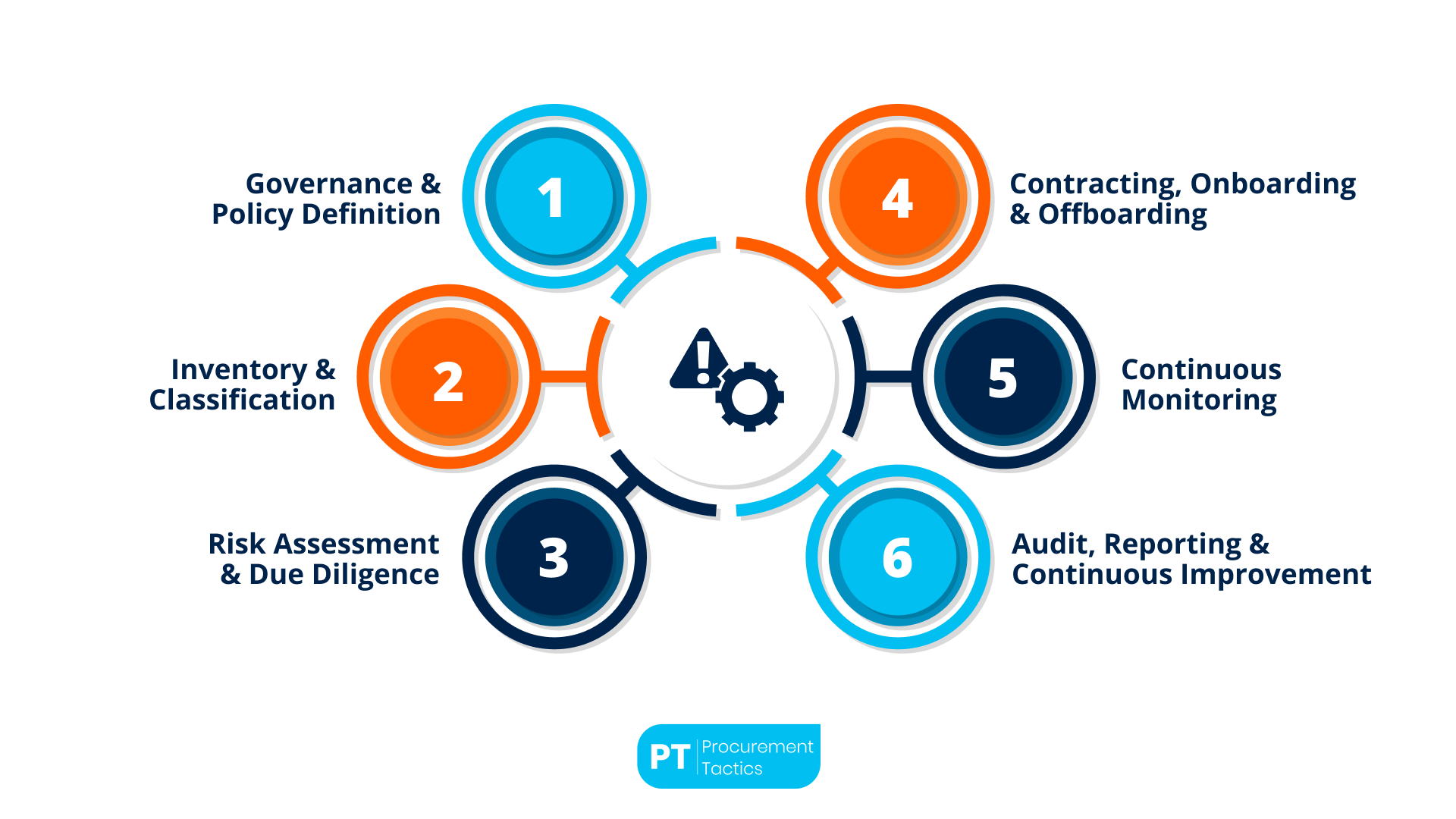
1. Governance & Policy Definition
Establish a formal Third-Party Risk Management framework that embeds vendor risk into your enterprise risk management and compliance programs. This includes defining clear roles and responsibilities, risk appetite, approval authorities, and escalation paths before any vendor is engaged.
Real-life Example - Microsoft
Microsoft folds vendor risk into its enterprise program through the Supplier Security & Privacy Assurance (SSPA) framework. Every supplier that will handle personal or confidential data must register in the SSPA portal, complete a risk questionnaire, and show evidence that it meets all 52 Data Protection Requirements before any purchase order is issued.
Non-compliant vendors are automatically blocked, and high-risk findings are escalated to Microsoft’s Security, Legal, and Privacy teams. Suppliers then re-attest to the same controls each year, giving Microsoft a continuous, board-visible view of third-party risk.
2. Inventory & Classification
Maintain a centralized inventory (“data map”) of all third parties, detailing the data, systems, and processes they access. Classify vendors into risk tiers—based on data sensitivity, business criticality, and access scope—to prioritize resources on high-risk relationships.
Real-Life Example - IBM OpenPages Third-Party Risk Management
IBM’s OpenPages platform keeps a single, enterprise-wide “vendor master” that lists every supplier, subcontractor, engagement, and contract in one repository.
During onboarding, vendors complete a risk questionnaire that feeds an inherent-risk engine; the system then auto-assigns a Low, Medium, or High criticality tier based on data sensitivity, business impact, and regulatory exposure.
Each tier drives the depth of due diligence, review cadence, and board reporting, so resources stay focused on high-risk relationships. Because inventory and risk scores live in the same system, any scope change or incident instantly re-scores the vendor and triggers escalations, giving IBM near-real-time visibility into third-party risk.
3. Risk Assessment & Due Diligence
Perform an initial evaluation using standardized questionnaires, documentation reviews, and, where warranted, on-site or remote audits. Assess each vendor’s cybersecurity posture, compliance with regulations, and operational resilience to determine the depth of due diligence required before contracting.
Real-life Example - Google’s Vendor Security Assessment (VSA) process
Before any contract is signed, Google makes suppliers complete two standardized questionnaires (Vendor and Project) that probe organisation-wide security and project-specific controls.
Responses feed a risk engine: higher-risk engagements must supply SOC 2 or ISO 27001 reports, allow an external SecurityScorecard scan, and—even for SaaS apps—undergo an independent penetration test.
Unresolved findings are logged in a shared remediation console and must be fixed before Procurement can raise a purchase order; sensitive projects also get an internal design review and extra contractual safeguards. This tiered workflow lets Google tailor due diligence depth to the vendor’s risk profile while keeping an auditable trail in one portal.
4. Contracting, Onboarding & Offboarding
- Contracting: Embed security, privacy, and performance clauses (e.g., SLAs, data-handling requirements) into vendor agreements.
- Onboarding: Standardize a process to educate vendors on your policies, verify required controls are in place, and document their attestation.
- Offboarding: Define steps to revoke access, return or destroy data, and formally close out contracts at the end of the relationship.
Real-life Example - Cisco’s Supplier Lifecycle
Cisco weaves security, privacy, and performance obligations into every vendor contract through its Supplier Data Protection Agreement (SDPA) and Supplier Information Security Exhibit (SISE), which spell out minimum controls, breach-notification timelines, SLA penalties, and audit rights.
During onboarding, each supplier must register in the Software & Services Supplier Portal, complete the SISE self-assessment, upload compliance evidence, and achieve “Approved” status before Procurement can release a purchase order.
At contract end, Cisco’s Service Portal automatically launches an Off-Boarding Process that revokes all system access, reclaims assets, and requires written confirmation that Cisco data has been returned or destroyed in accordance with NIST SP 800-88, giving the Vendor Risk Office a fully auditable close-out.
5. Continuous Monitoring
Leverage automated tools and security-rating services to track changes in vendor control environments, compliance status, and emerging threats in real time. Continuous monitoring enables proactive detection of risk threshold breaches rather than relying solely on periodic assessments.
Real-life Example - Mastercard’s RiskRecon continuous monitoring
Mastercard keeps a live watch on more than 13,000 suppliers through its RiskRecon platform (a Mastercard company). The tool refreshes each vendor’s cybersecurity rating every 24 hours across 10 control domains and flags drops below a preset “B” threshold. Those alerts flow straight into Mastercard’s ServiceNow queue, where the Third-Party Cyber Risk Office opens remediation tickets and, for critical vendors, auto-escalates to the CISO.
Because ratings, vendor inventories,and workflow all sit in the same portal, any newly discovered vulnerability, data leak, or scope change instantly re-scores the supplier and updates board dashboards—giving leadership real-time, portfolio-wide visibility instead of waiting for annual assessments.
6. Audit, Reporting & Continuous Improvement
Schedule regular internal audits and performance reviews of your vendor ecosystem. Analyze monitoring data and audit findings to refine policies, update risk thresholds, and enhance controls, ensuring the Third-Party Risk Management program evolves alongside business needs and regulatory changes.
Real-life Example - Bank of America
Bank of America folds audit, reporting, and continuous-improvement loops into its Third-Party Risk program:
- Three-line audit cadence. Corporate Audit (the third line of defense) performs independent reviews of both first- and second-line vendor-risk controls, validating testing results and tracking corrective actions to closure.
- Quarterly board-level reporting. The Enterprise Risk Committee and full Board receive quarterly dashboards that show key metrics—vulnerability counts, third-party incidents, and risk-appetite breaches—and stay on the incident report until every action item is resolved.
- External assessments drive improvement. The bank regularly hires third-party assessors and consultants to test control effectiveness. Findings feed back into policy updates and risk-threshold adjustments, ensuring the framework evolves with new threats and regulations.
Third-Party Risk Management – 7 Best Practices
Third-party risk management is an essential component of every organization’s risk management strategy, especially in today’s digitally interconnected world, where reliance on external suppliers is constantly increasing.
Effective third-party risk management enables organizations to identify, assess, and mitigate risks arising from relationships with third parties such as suppliers, partners, and service providers.

1. Define Clear Objectives and Scope
The first step towards an effective third-party risk management program is clearly defining its objectives and scope. Organizations should identify all third parties they engage with and classify them based on their risk levels.
Classification factors may include access to sensitive data, criticality of the services provided, and geographic location. For example, a software provider with access to confidential data typically represents a higher risk than an office supplies vendor.
2. Risk Assessment and Due Diligence
Before engaging with a third party, conducting thorough risk assessments and due diligence is crucial. This process involves analyzing security policies, regulatory compliance history, and the financial stability of the prospective partner. Using standardized questionnaires and templates can help systematize this process effectively.
3. Continuous Monitoring and Reevaluation
Risks associated with third parties are dynamic and can evolve over time. Thus, organizations should implement mechanisms for continuous monitoring of third-party performance and compliance. Regular audits, security incident tracking, and periodic risk reassessment are essential practices for effective ongoing oversight.
4. Integration into Broader Risk Management Strategy
Third-party risk management should not function in isolation; rather, it must be an integrated component of an organization’s broader risk management strategy.
Effective integration requires collaboration across various departments such as IT, legal, procurement, and compliance, ensuring comprehensive protection against potential threats.
5. Leverage Technology for Automation and Efficiency
Implementing technological solutions can significantly enhance the efficiency and accuracy of third-party risk management processes. Risk management platforms automate risk assessments, compliance monitoring, and real-time reporting, reducing manual work and enhancing responsiveness to emerging threats.
6. Employee Training and Awareness
Employees represent the first line of defense against third-party risks. Regular training on third-party risk management policies and procedures ensures that staff can identify and report suspicious activities effectively, thereby fostering a robust security culture within the organization.
7. Incident Response and Business Continuity Planning
Despite proactive measures, incidents involving third parties can still occur. Organizations should therefore have clearly defined incident response and business continuity plans in place. These plans should cover scenarios such as supplier disruptions, security breaches, and other crisis situations, helping minimize potential operational impacts.
Examples of Third-Party Security Risks
1. SolarWinds Supply Chain Attack
Case: In 2020, the SolarWinds supply‑chain attack demonstrated how a single compromised vendor can cascade across thousands of customers. Attackers embedded the SUNBURST backdoor into Orion software updates, which were downloaded by roughly 18,000 organizations—including multiple U.S. federal agencies and Fortune 500 firms—giving the intruders privileged access to internal networks and sensitive data.
Solution:
Key lessons for preventing similar third‑party software breaches include:
- Demand software transparency and verification. Require vendors to provide a signed Software Bill of Materials (SBOM) and validate all updates with cryptographic code‑signing checks before deployment.
- Harden access with zero‑trust principles. Limit every vendor application—especially monitoring tools like Orion—to the minimum privileges and network segments they truly need, and continuously authenticate both users and devices.
- Embed third‑party cyber clauses and audits in contracts. Contracts should mandate regular security attestations, right‑to‑audit, and prompt disclosure of incidents; vendors that fall short face termination or remediation requirements.
- Monitor suppliers in real time. Pair traditional vulnerability assessments with continuous telemetry (e.g., attack‑surface management, threat‑intel feeds) so anomalous behavior in vendor software triggers immediate containment.
- Patch fast—assume compromise. Maintain an emergency patch playbook and layered defenses so that even if a malicious update slips through, the “blast radius” is contained and rapid recovery is possible.
2. Target Data Breach via HVAC Vendor
Case: In 2013, retail giant Target suffered a breach that exposed 40 million payment‑card numbers and up to 70 million customer records. Attackers first stole remote‑access credentials from Fazio Mechanical, Target’s HVAC contractor, then used that foothold to traverse the network and install RAM‑scraping malware on point‑of‑sale systems, siphoning card data in real time.
Solution:
Key controls to stop or contain vendor‑originated intrusions include:
- Restrict vendor privileges and segment networks. Confine suppliers to the narrowest possible access and isolate sensitive assets (e.g., POS devices) with VLANs or zero‑trust micro‑segmentation.
- Enforce strong authentication and credential hygiene. Require multi‑factor authentication on every third‑party connection, rotate passwords frequently, and monitor for credential reuse or leaks.
- Embed rigorous third‑party due diligence clauses. Contracts should mandate security attestations, right‑to‑audit, breach‑notification SLAs, and immediate remediation or termination options for non‑compliant vendors.
- Continuously monitor vendor activity. Pair vulnerability scanning with real‑time telemetry and anomaly detection so any unusual supplier behavior triggers rapid investigation.
- Maintain rapid‑containment playbooks. Be able to disable vendor connections, rotate credentials, and patch critical systems at short notice to limit the blast radius if a compromise occurs.
3. Slack and Microsoft Teams Third-Party App Vulnerabilities
Case: Recent academic research—most visibly a University of Wisconsin‑Madison study—showed that third‑party apps for Slack and Microsoft Teams frequently request broad OAuth scopes that let them read private channels, post on behalf of users, or exfiltrate files. Because neither platform performs a full source‑code audit and developers can push new code after publication, a benign app can later turn malicious, enabling supply‑chain attacks that silently sweep through entire workspaces.
Solution:
- Adopt a least‑privilege, allow‑listing model. Block blanket installations; require security teams to pre‑approve each app and strip unneeded OAuth scopes before granting access.
- Enable app‑governance tooling. Microsoft Defender for Cloud Apps and similar SaaS‑security platforms surface risky OAuth tokens, anomalous behavior, and excessive permissions so admins can quarantine or revoke apps in real time.
- Mandate continuous code integrity checks. Require vendors to sign releases and hash manifests, then verify those hashes automatically on every update to prevent post‑approval code swaps.
- Set conditional‑access and session-control policies. Pair MFA with context‑aware access, block high‑risk countries, and log every API call an app makes for rapid anomaly detection.
- Embed security clauses in app marketplace agreements. Demand rapid‑patch SLAs, right‑to‑audit, and clear incident‑notification timelines; apps that fail periodic reviews are delisted until issues are fixed.
Conclusion
Third‑party Risk Management safeguards an organization’s extended ecosystem by systematically identifying, assessing, and controlling vendor‑related threats. A mature Third‑party Risk Management program starts with clear governance and risk appetite, maintains an up‑to‑date inventory of suppliers, applies proportionate due diligence and contractual controls, and relies on automated, continuous monitoring.
Integrating Third‑party Risk Management with broader enterprise‑risk processes—and reinforcing it through employee training and periodic audits—shortens detection‑to‑response time, limits financial and reputational impact, and ensures sustained compliance in an increasingly interconnected world.
Frequentlyasked questions
What Is Third-Party Risk Management?
Third-party risk management is a framework that keeps your entire vendor ecosystem aligned with your company’s risk appetite and legal obligations throughout onboarding, ongoing operations, and offboarding.
Why is Third‑Party Risk Management (TPRM) essential today?
Outsourced services widen your attack surface and regulatory exposure. TPRM gives continuous visibility into vendor security and compliance, cutting the likelihood and impact of supplier‑driven breaches or fines.
How often should we reassess a vendor’s risk profile?
High-risk items require continuous monitoring along with an annual review. Medium-risk items should be reviewed every 18 to 24 months. Low-risk items need to be assessed every 2 to 3 years, or immediately if a major change or incident occurs.
About the author
My name is Marijn Overvest, I’m the founder of Procurement Tactics. I have a deep passion for procurement, and I’ve upskilled over 200 procurement teams from all over the world. When I’m not working, I love running and cycling.










